AWS IAM Multi-Factor Authentication (MFA)
What is AWS multi-factor authentication (AWS MFA)?
AWS IAM Multi-Factor Authentication (MFA), in this Tutorial one, you can learn AWS IAM Multi-Factor Authentication (MFA). Are you the one who is looking for the best platform which provides information about AWS IAM Multi-Factor Authentication (MFA)? Or the one who is looking forward to taking the advanced Certification Course from India’s Leading AWS Training institute? Then you’ve landed on the Right Path.
The Below mentioned Tutorial will help to Understand the detailed information about AWS IAM Multi-Factor Authentication (MFA), so Just Follow All the Tutorials of India’s Leading Best AWS Training institute and Be a Pro AWS Developer.
AWS multi-factor authentication (AWS MFA) provides an extra level of security that you can apply to your AWS environment. You can enable AWS MFA for your AWS account and for individual AWS Identity and Access Management (IAM) users you create under your account.
Introduction
♦ With MFA enabled, when a user signs in to an AWS website, they will be prompted for their user name and password (the first factor -> what they know)
♦ As well as for an authentication response from their AWS MFA device (Smartphone or tablet, the second factor -> what they have). By integrating, these multiple factors provide increased security for your AWS account settings and resources.

♦Amazon MFA adds additional security as a result of it needs users to type a distinctive authentication code (one-time password or access key) from an approved authentication device (Smartphone or Tablet) or SMS (Short Message Service) text message once they access AWS websites or services.
♦Why AWS multi-factor authentication?
AWS Multi-Factor Authentication used because of its high-level security and advantages stated below:
♦Enhanced Security in every manner.
Granular Control.
♦Temporary Credentials.
Flexible Credentials and Security Management.
♦Integration with AWS services.
Leverage external identity system.
Prerequisites to apply multi-factor authentication to your account
♦Virtual MFA Applications:
You can use a mobile device, such as a Smartphone or tablet, as a virtual multi-factor authentication (MFA) device. To do this, install an AWS supported app on mobile that generates a six-digit authentication code (one-time password). You will not have to pay for this service.
You have to install virtual MFA apps as per your Smartphone OS listed below:

PERMISSIONS REQUIRED:
TO manage virtual MFA devices for your IAM user, you must have set the permissions policy to authenticatedIAM Users to Manage for edit Their Own MFA Device means to allows users to manage their own credentials with MFA or not.
♦You can enable MFA device for your AWS account and for individual IAM users you have created under your group in your account. MFA can be also be used to control access to AWS services APIs.
After you’ve obtained a supported U2F security key, hardware device, or virtual MFA device, AWS does not charge any additional fees for using MFA.
♦You can also protect cross-account access using MFA.
There are two types of Amazon MFA: Security Token-Based and SMS Text Message-Based.
►Steps To enable a virtual MFA device for an IAM user (console):
- Sign in to the AWS Management Console and open the IAM console at https://console.aws.amazon.com/iam/.
2. In the navigation pane, choose Users.
3. In the User Name list, select the name of the intended MFA user.
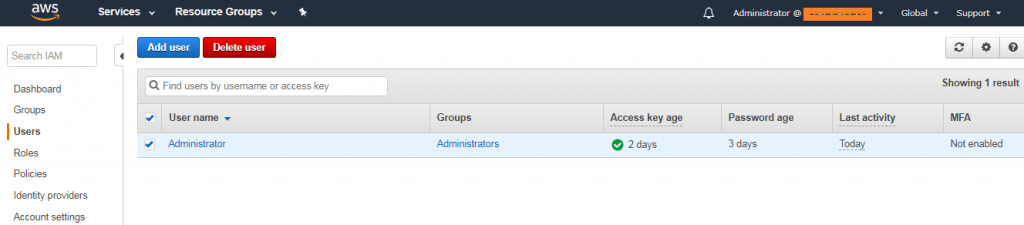 4. Choose the Security credentials Next to Assigned MFA device, choose Manage.
4. Choose the Security credentials Next to Assigned MFA device, choose Manage.
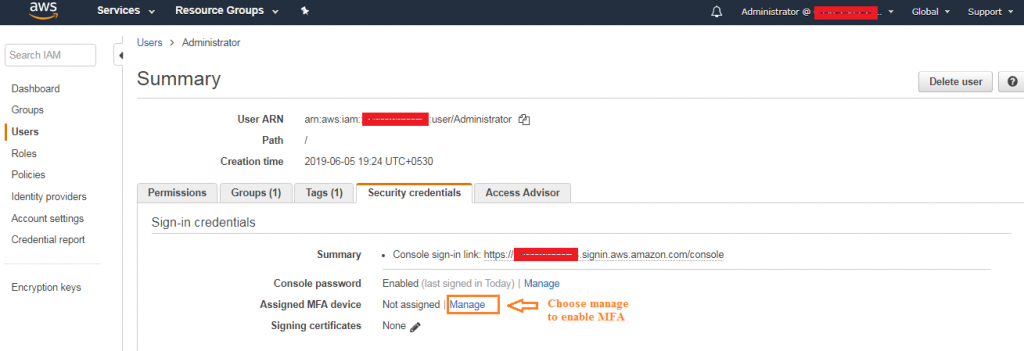
5. In the Manage MFA Device wizard, choose Virtual MFA device, and then choose Continue.
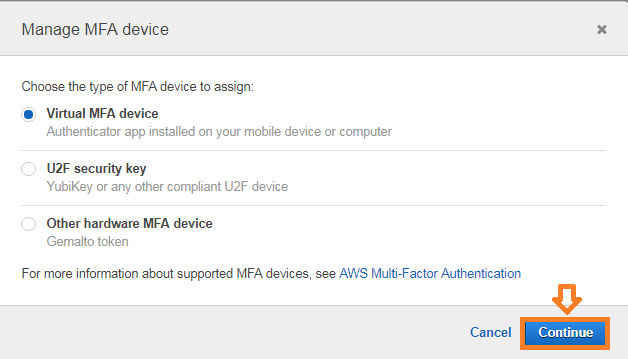
6. Open your virtual MFA app on
7. Determine whether the MFA app supports QR codes, and then do one of the following:
From the wizard, choose Show QR code, and then use the app to scan the QR code. For example, you might use the camera icon or click an option similar to Scan code, and then use the device’s camera to scan the QR code if your device supports it. In the Manage MFA Device dialog box, click on Show secret key and then type the secret key into your MFA device app
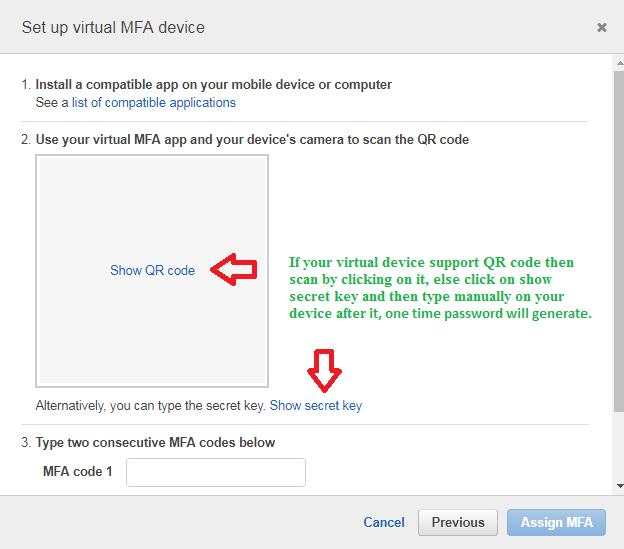
When you are finished, the virtual MFA device starts generating an authentication code (one-time passwords).
- In the Manage MFA Device dialog box, in the MFA code 1 box, type the one-time password that currently appears in the virtual MFA device app. Wait up to 30 seconds for the device to generate a new authentication code (one-time password). Then type the second one-time password into the MFA code 2 box that you got after first code. Click on the Assign MFA button.
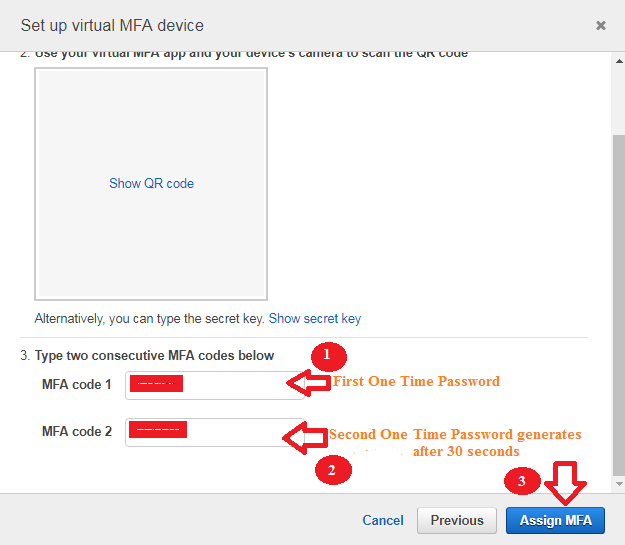
Important: Submit your request immediately after generating the codes. If you generate the codes and then wait too long to submit the request, the MFA device successfully associates with the user but the MFA device is out of sync means time out. This happens because of time-based one-time passwords (TOTP) expire after a short period of time. If this happens, you can try again to connect the device.
The virtual MFA device is now ready for use with AWS services
♦You can also use the AWS Management Console to configure and enable a virtual MFA device for your root user.
To enable MFA devices for the AWS account, you must be signed in to AWS using your root user credentials (E-mail ID & Password).
♦You cannot enable an MFA device for the AWS account root user in the IAM console or with the AWS CLI, AWS API, Tools for Windows Power Shell, or any other command-line tool.
If your MFA device (Smartphone or Tablet) is lost, stolen, or not working, you can still sign in using alternative factors of authentication.
I hope you have learned how to enable a virtual MFA device (Smartphone or tablet) for an IAM user and also learned AWS Multi-factor Authentication